Third-Party Cyber Risk Management (TPRM)
Automate, unify and run your TPRM program at scale.
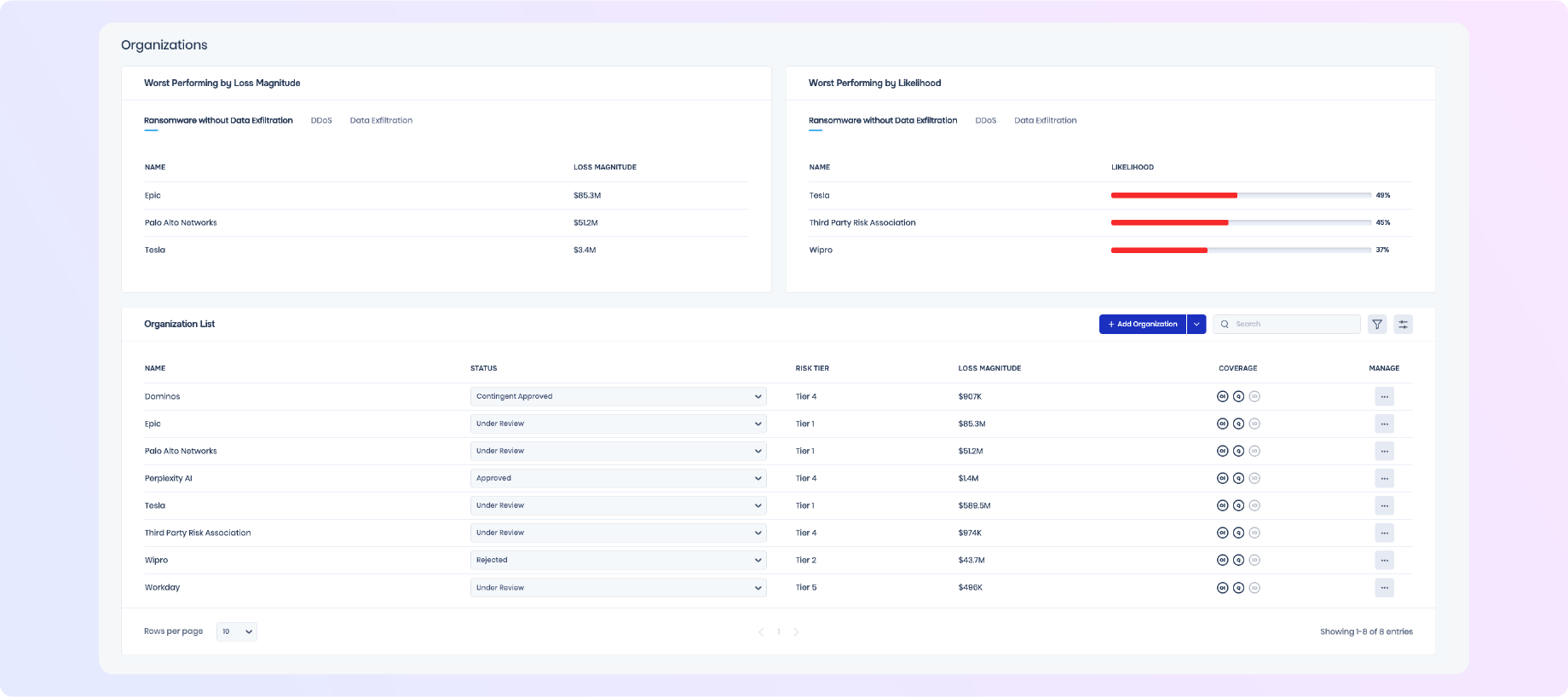

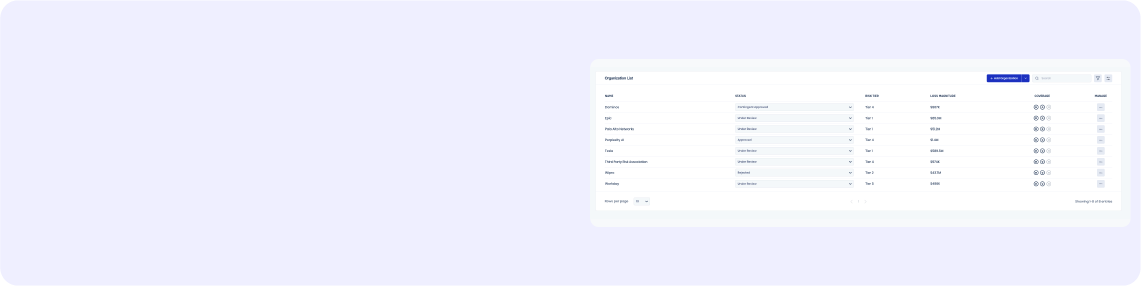
Risk-Based TPRM
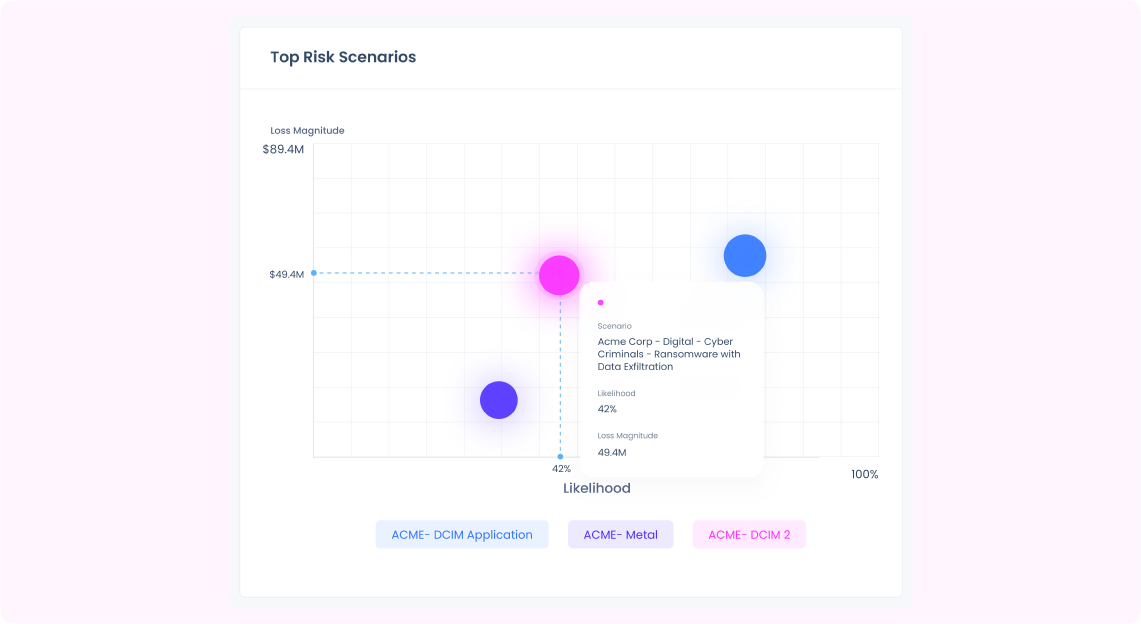
Third-party risk quantified in financial terms
Third-party tiering based on loss exposure
Prioritized third-party risk mitigations
Continuous assessment of control effectiveness
ROI-driven third-party
risk analysis
Out-of-the-box dashboards
and reports
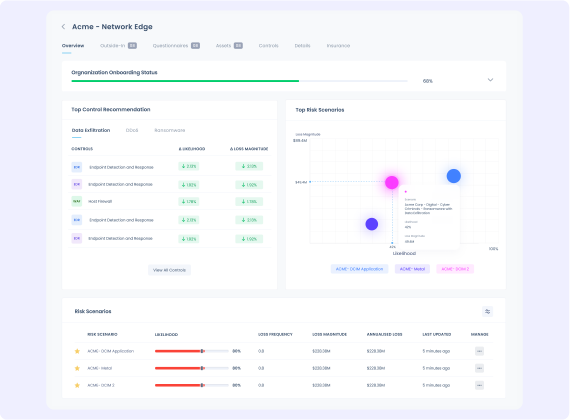
Unified Third-Party Cyber Risk Management Platform
- Integrated third-party plus first-party cyber risk
- Outside-in, Questionnaire, Inside-out & Zero-trust TPRM
- Contextualized with external threat intelligence
Build, Scale, and Automate Your TPRM
Real-time “inside-out”
third-party risk monitoring

Automated data collection and processing
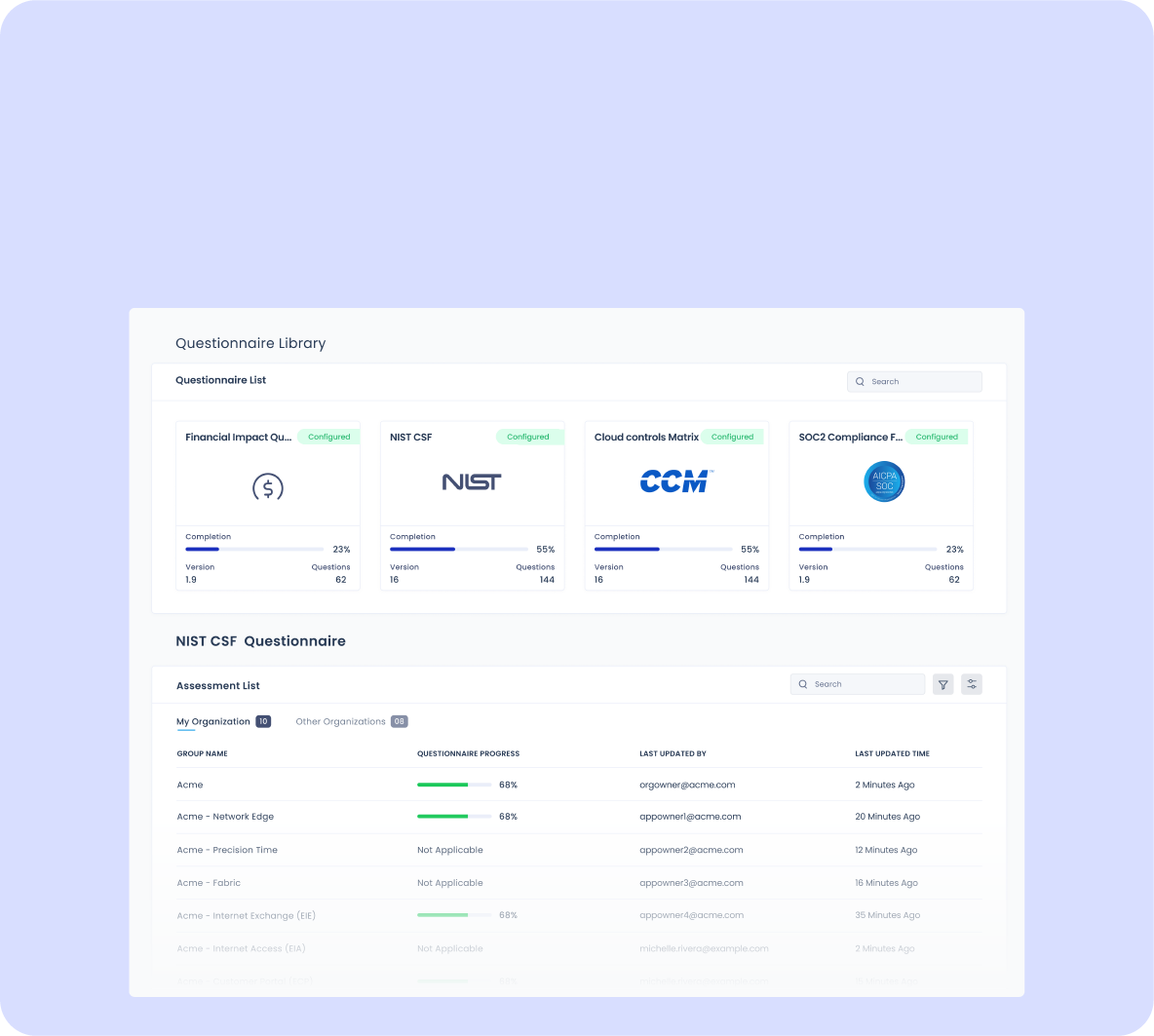
Marketplace-driven questionnaire automation

Best-in-class risk advisory
services with ongoing trainings,
education, & certifications
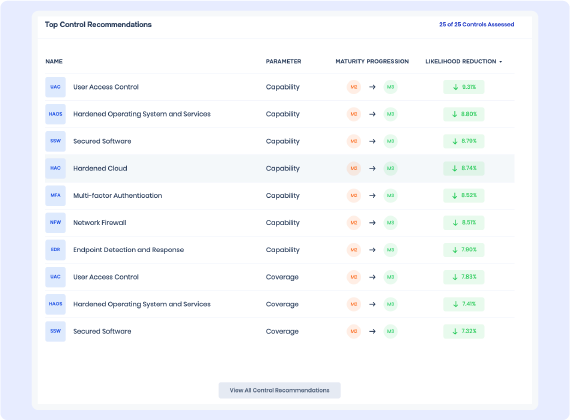
Zero-Trust Driven Data for Organizational Controls
Know how well your first-party controls are configured to minimize third-party breaches
- Real-time native control scans
- Efficient resource allocation
- Informed decision-making
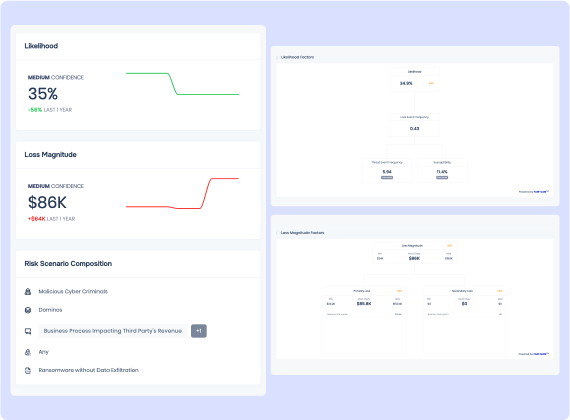
Purpose-Built on Proven, Industry-Leading, Open Standards
- FAIRTM, FAIR-TAM, FAIR-CAM, FAIR-MAM
- Mapping to MITRETM ATT&CK & D3FEND
- Transparent, defensible outputs
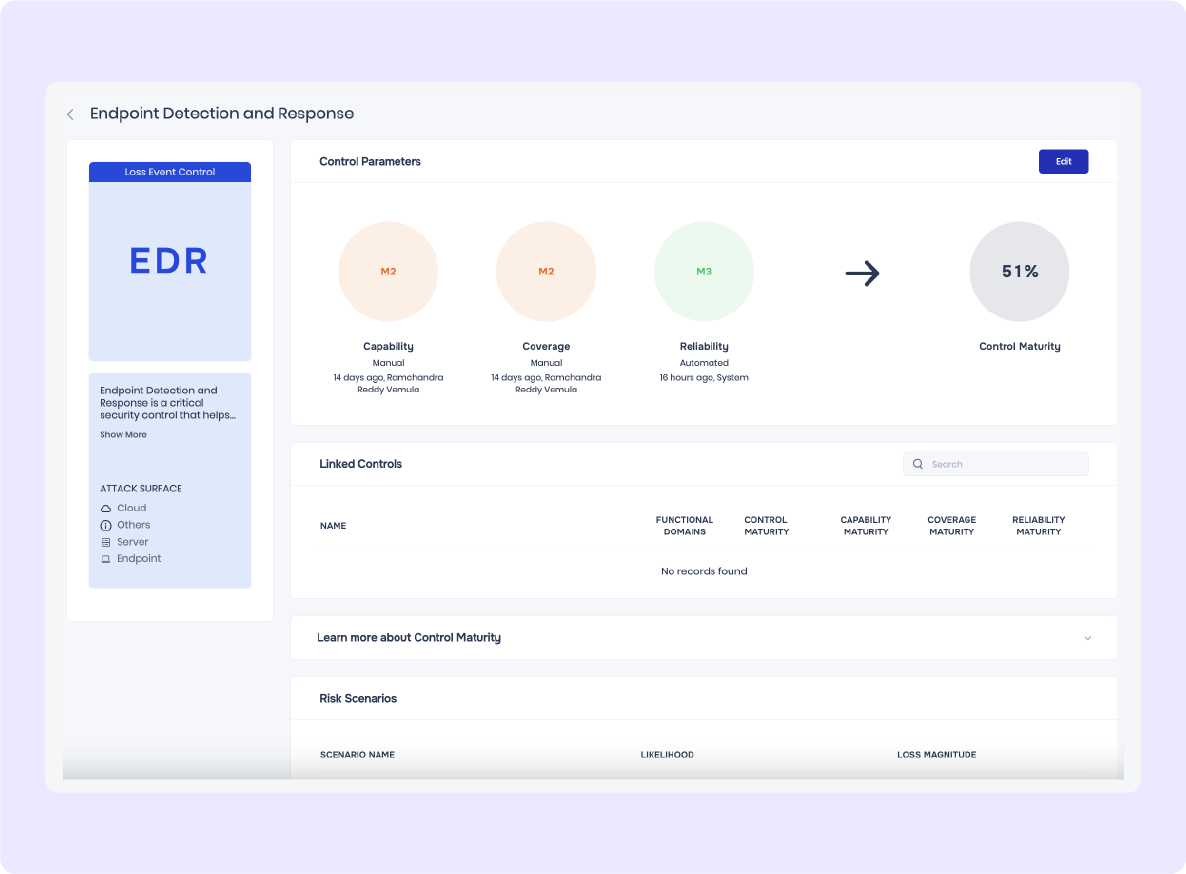
Reduce and Optimize TPRM Cost
- Reduced cost with software stack consolidation
- Increased third-party coverage at a predictable cost
- Optimized TPRM administrative costs